The Russian invasion of Ukraine in February 2022 led to questions over the impact that cyber attacks were likely to have during the conflict. This box looked at the history of cyber-related activity in the region, and the evidence available for cyber impacts of the conflict to date.
This box is based on Microsoft data from April 2022 .
The period following the annexation of Crimea by Russia in 2014 was characterised by sustained cyber-attacks against key Ukrainian infrastructure by Russian-linked groups. In November 2015, the Ukrainian power grid was hacked by groups allegedly linked to Russia, leaving an estimated 230,000 customers in Western Ukraine without power for up to six hours.a The successful attack in 2015 was followed up by the NotPetya ransomware attack of 2017 (discussed above), where the total cost of the attack was estimated at nearly $10 billion globally. The White House dubbed the attacks as the “most destructive and costly cyber-attack in history”.b The ‘NotPetya’ attack was also the first time Western officials publicly attributed a cyber-attack to groups linked to the Russian government, with the National Cyber Security Centre (NCSC) in the UK releasing a statement to this effect in 2018.c
The run-up to the next Russian invasion of Ukraine in early 2022 also saw continued cyber-attacks from Russian-linked groups, though at a much smaller scale in comparison to the major attacks witnessed in 2015 and 2017. Ukrainian government officials reported in January 2022 that an estimated 288,000 cyber-attacks were recorded in the first 10 months of 2021, on top of the 397,000 attacks that had been recorded in 2020.d
Against this backdrop, many analysts had expected cyber-attacks to feature heavily in the conflict following the full-scale invasion of Ukraine in February 2022. It has been argued by some commentators that Russia has so far refrained from large-scale cyber-attacks against Ukraine because the Russian military were also making use of the infrastructure in the country.e
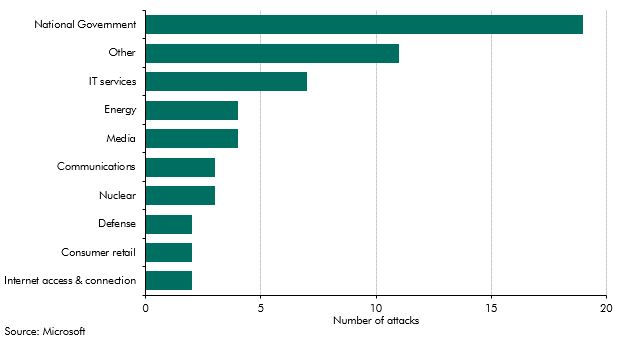
Despite the war remaining largely conventional to date, it appears that cyber-attacks have played more of a role in the conflict than initially realised. There have been reported cases of Russian cyber activity just before the invasion, including attacks on Ukrainian and European satellite communication systems in late February.f And in March there were more attacks as the war intensified, including the hacking of a Ukrainian nuclear power plant and the breach of a Kyiv-based media agency that had its data stolen by Russian-linked hackers.g More recent analysis by Microsoft suggests a correlation between military advances and cyber activity (Chart A sets out the number of these attacks, by sector of the economy targeted).h Another indirect aspect of cyber risk that has played a role in the conflict is in the form of disinformation. Although many Russian state outlets were banned on Facebook and Twitter, there are continued allegations of the promotion of false narratives online, through social networks and video platforms.,sup>i
Chart A: Cyber-attacks on Ukraine by Russia since the invasion began, by sector
It remains unclear whether the lack of a catastrophic cyber-attack related to the conflict stems from Russia’s choice of offensive tactics, Ukraine’s defensive capability, or evidence that such attacks are harder to mount or less impactful than previously thought. However, as this is a report focused on risks to the outlook, and in the absence of more information to substantiate the first two hypotheses, it takes as its starting assumption that a major, successful cyber-attack on the UK remains a material threat and looks to estimate its potential economic and fiscal consequences later in this chapter.
This box was originally published in Fiscal risks and sustainability – July 2022
